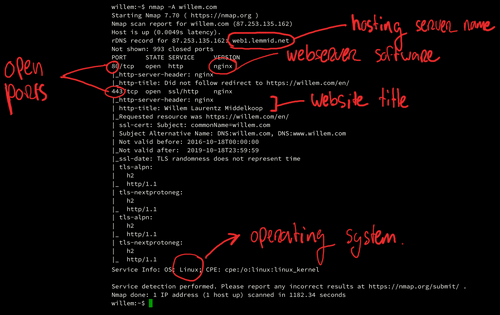
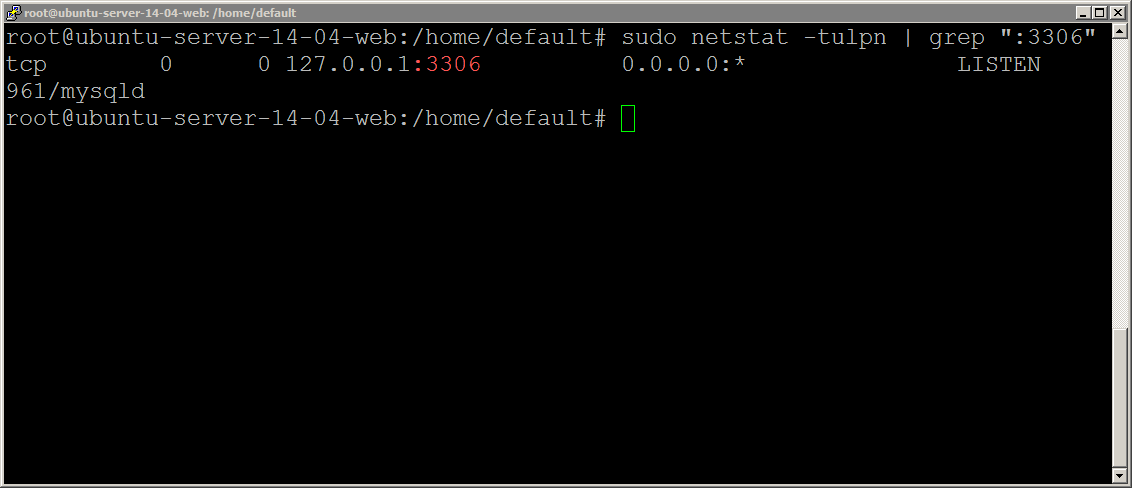
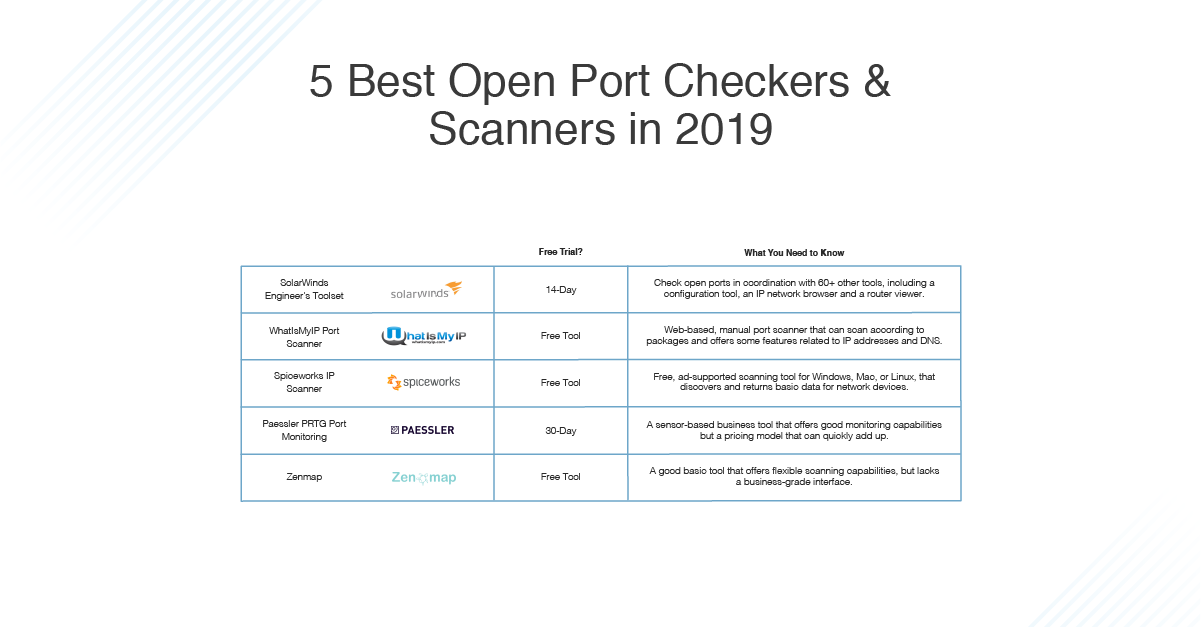
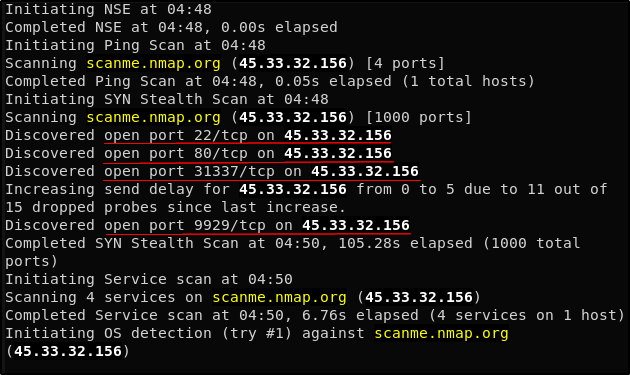
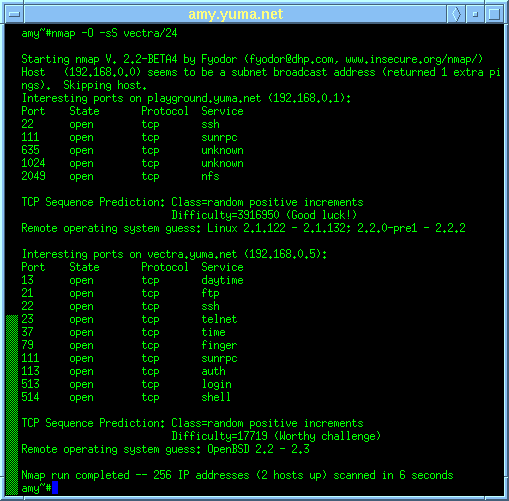
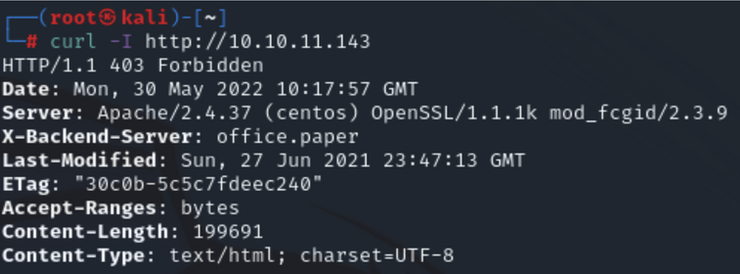
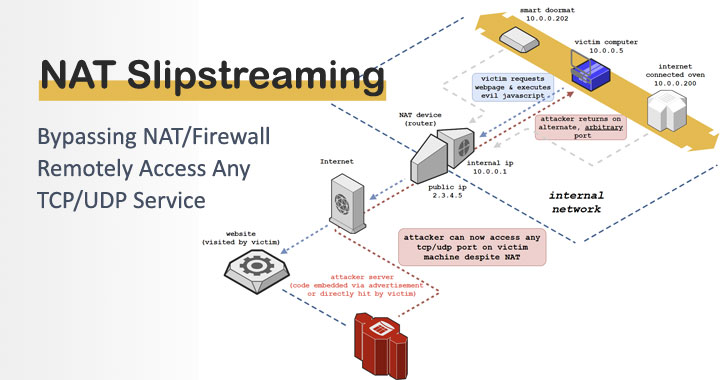
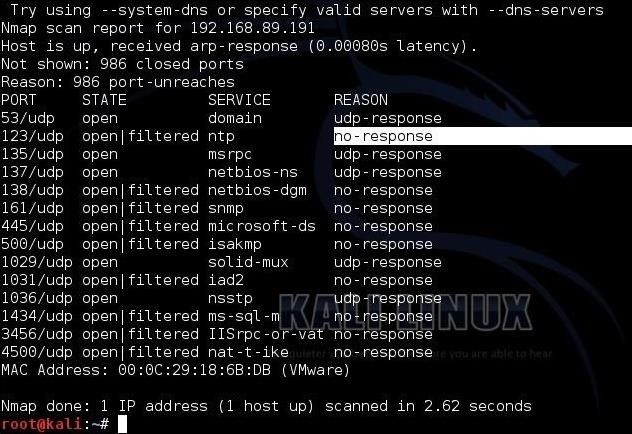
Day 46: How Do Hackers Use Open Ports To Perform Attacks? | Day 46: How Do Hackers Use Open Ports To Perform Attacks? Today I will discuss: 1. Why do hackers search

Hundreds of popular Android apps have open ports, making them prime targets for hacking | TechRepublic

Metasploitable 2: Port 80. Welcome back to part IV in the… | by Miguel Sampaio da Veiga | Hacker Toolbelt | Medium